In today’s digital world, network security is essential, and it’s crucial to know what weaknesses exist in your system. Nmap (Network Mapper), an adaptable and free tool for network research and security audits, is one strong tool that sticks out in this field. Nmap provides users with important insights into potential vulnerabilities by skillfully searching a target system for open ports. This enables users to take proactive steps to protect against potential threats and unauthorized access. Apart from this to transmit or receive data over the network opening a port on Linux is essential.
Many aspiring system administrators find networking to be a vast and intimidating subject. To comprehend them, one needs to become proficient with a variety of tools and utilities in addition to a wide range of layers, protocols, and interfaces.
Ports are logical communication endpoints in TCP/IP and UDP networking. Numerous web servers, application servers, and file servers, might operate on a single IP address. Each of these services needs a specific port to listen on and use for communication. Both an IP address and a port are connected when you establish a connection with a server.
Comprehending Ports
The OSI networking model has numerous layers. The layer that deals with communication between various services and applications is known as the transport layer. The primary layer with which ports are associated is this one.
For network traffic, ports on contemporary operating systems have numbered addresses. By default, different ports are used by different types of services.
For instance, POP3 email uses port 110, but ordinary web traffic uses port 80. A firewall can function, among other things, by permitting or blocking traffic over a specific port.
Examining Available Ports
You may check for open ports using a variety of programs. Netstat is one that comes pre-installed on the majority of Linux variants.
Using the following options, you can easily find out which services you are running by performing the following command:
sudo netstat -plunt
The following outcomes are what you’ll observe:
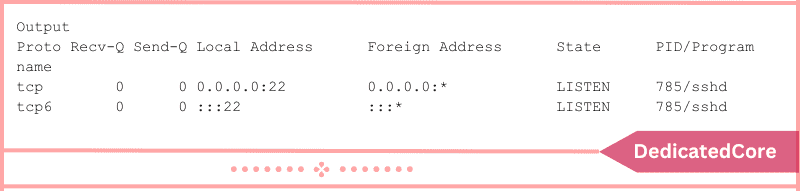
This lists both TCP and UDP protocols together with the port and listening socket connected to the service. Another program you can use to find ports is called nmap.
Port Scanning Using Nmap
Numerous details about a host can be found with Nmap. Additionally, it may lead system administrators of the target system to believe that someone is doing maliciously. Because of this, you should only test it on servers you own or in circumstances where you have informed the owners. The test server, scanme.nmap.org, is made available by those who created Nmap.
For nmap practice, this or your servers are good targets.
These are a few typical tasks that nmap may accomplish. To prevent some queries from producing partial answers, we shall execute them all with sudo privileges. Certain commands might take a very long time to finish:
Check for the operating system on the host:
sudo nmap -O scanme.nmap.org
Ignore the part about network discovery and presume that the host is online. This is helpful if your previous tests yield a response stating, “Note: Host seems down.” Include this with the other choices:
sudo nmap -PN scanme.nmap.org
Do a scan without using the provided IP address for a reverse DNS lookup. In most circumstances, this should expedite your results:
sudo nmap -n scanme.nmap.org
Scan a single port as opposed to all of the popular ports:
sudo nmap -p 80 scanme.nmap.org
Nmap can establish a three-way handshake (described below) with the specified port to search for TCP connections. Carry it out as follows:
sudo nmap -sT scanme.nmap.org
Enter to look for UDP connections:
sudo nmap -sU scanme.nmap.org
Check for all available TCP and UDP ports:
sudo nmap -n -PN -sT -sU -p- scanme.nmap.org
A TCP “SYN” scan makes use of the way TCP creates connections.
The requesting end sends a “synchronize request” packet to the server to establish a TCP connection. Subsequently, the server replies with a “synchronize acknowledgment” packet. A connection is then made when the initial sender replies to the server with an “acknowledgment” packet.
However, as soon as the server returns the first packet, a “SYN” scan breaks the connection. This kind of scan, known as a “half-open” scan, was once advertised as a covert method of looking for ports because the program connected to that port would never get any communication because the connection would never finish.
With the deployment of increasingly sophisticated firewalls and the flagging of incomplete SYN requests in many settings, this is no longer seen as covert.
To do a SYN scan, click on:
sudo nmap -sS scanme.nmap.org
Sending invalid TCP headers—which, provided the host complies with TCP rules, should send a message back if that port is closed—is a more covert method. Servers that are not Windows-based can use this.
The flags “-sF”, “-sX”, or “-sN” are usable. Each of them will yield the desired outcome:
sudo nmap -PN -p 80 -sN scanme.nmap.org
Use this command to find out the version of a service that is active on the host. It tests various server answers in an attempt to identify the service and version:
sudo nmap -PN -p 80 -sV scanme.nmap.org
Lastly, nmap can be used to scan several devices at once. Use a command similar to the following to specify a range of IP addresses with “-” or “/24” to scan many hosts at once:
sudo nmap -PN xxx.xxx.xxx.xxx-yyy
Use a command similar to this to search a network range for available services:
sudo nmap -sP xxx.xxx.xxx.xxx-yyy
While there are many more command combinations available, this should help you begin to identify any potential networking issues.
Final Thoughts on Using Nmap to Scan for Open Ports
In conclusion, anyone interested in network security should become proficient in using Nmap to search for open ports. This adaptable tool gives users the ability to successfully strengthen their defenses in addition to offering a thorough view of the system’s exposure.
Nmap is a vital ally in the continuous fight to defend our digital surroundings because as technology advances, so do potential adversaries’ tactics. You ensure the resilience and integrity of your network infrastructure by being proactive and using Nmap in your security toolkit. Securing your data and your VPS requires more than just knowing how to configure ports and identify attack vectors on your server.
Still, it’s a necessary talent. You can lock down your server by finding out which ports are open and what information can be retrieved from the services that are allowing connections on those ports. Any unnecessary data that leaks from your computer could be utilized by a hostile user to try and take advantage of vulnerabilities already known or create new ones. It’s best if they can’t find out too much.

