Configuring up Nginx as a reverse proxy on Ubuntu 22.04 is a crucial ability to improve security and web server performance. Reverse proxy functions are well-managed by Nginx, a web server with great performance. Versatility that is well-liked by many administrators and developers. This tutorial aims to give users utilizing the most recent Ubuntu release, 22.04. A clear and simple way to utilize Nginx as a reverse proxy. Choosing a Canadian vendor for vps hosting ensures compliance with local regulations and offers improved reliability for users.
For detailed guidance on setting up and configuring Nginx on Ubuntu 20.04, including server block configuration and firewall adjustments, check out our step-by-step installation guide. It is advised to use a reverse proxy to make an application server publicly accessible. Whether you are using a small built-in web server with Flask or a production-grade Node.js application. These application servers will frequently bind to localhost using a TCP port. This implies that your application will only be available locally on the computer it is installed on by default.
The VDS hosting is ideal for running intensive workloads of any sized enterprise and individuals with the latest processor. Communicating with a reverse proxy is identical to communicating directly with the application server from the client’s point of view. The client cannot distinguish between them because they both function in the same way. Without the need for additional configuration on the part of the client, a resource is requested and then provided.
Requirements:
- The application server address that you wish to proxy; will be known as app_server_address for the duration of the tutorial. This can be either a Unix domain socket (such as http://unix:/tmp/pgadmin4.sock for pgAdmin) or an IP address with a TCP port (such as the Gunicorn default of http://127.0.0.1:8000). Should you be testing without an application server configured? you will be walked through the process of configuring a Gunicorn application that will bind to http://127.0.0.1:8000.
- An address that points to the public IP of your server. This will be set up to proxy your application server using Nginx.
Configure Nginx as a Reverse Proxy on Ubuntu 22.04
Step 1: Installing Nginx at First
You can use apt to install Nginx using the default repositories. After updating the repository index, install Nginx:
$ sudo apt update $ sudo apt install nginx
To verify the installation, press Y. Press ENTER to accept the defaults if you are prompted to restart services.
Your firewall needs to permit access to Nginx. After configuring your server in accordance with the initial server requirements, use ufw to add the following rule:
$ sudo ufw allow 'Nginx HTTP'
You may now confirm that Nginx is operational:
$ systemctl status nginx

You will then include your domain and app server proxy in a custom server block.
Step 2: Setting Up Your Server Block.
Creating a custom configuration file for your new server block additions is advised over merely modifying the default setup. Using nano or your favorite text editor, create and open a new Nginx configuration file:
sudo nano /etc/nginx/sites-available/your_domain
Replace your_domain and app_server_address with the following information when you insert it into your new file. For the optional Gunicorn server configuration in Step 3, use http://127.0.0.1:8000 by default if you don’t have an application server to test with.

In nano, you can save and leave by pressing CTRL+O followed by CTRL+X.
This configuration file starts with a typical Nginx setup, meaning that requests to your_domain. As www.your_domain will be answered by Nginx listening on port 80. The proxy_pass directive in Nginx is used to enable reverse proxy capabilities. This setup will allow you to open app_server_address on your remote computer. Navigate to your_domain in your local web browser. Although Nginx can act as a proxy for numerous servers at once. This tutorial will only cover one application server. A single server name can integrate several application servers. Through a proxy create a single, coherent web application by adding extra location blocks as needed.
Headers, which include details about the client sending the request, are attached to every HTTP request. This contains information on the user’s IP address and cache settings. Also with cookie tracking, authorization status, and other things. The following header forwarding settings are suggested by Nginx. That is included in proxy_params; the specifics are located in /etc/nginx/proxy_params.
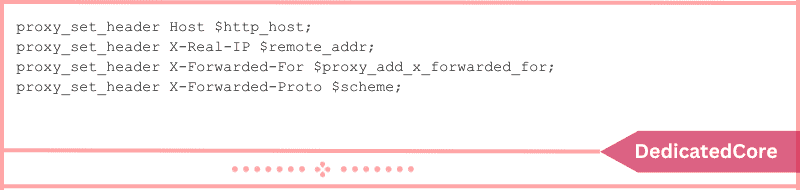
Your objective while using reverse proxies is to transmit pertinent client information. As well as occasionally server information. However, there are situations in which a proxied server would need to know which reverse proxy server processed the request. Most of the time the crucial data comes from the request made by the original client. Nginx makes use of the proxy_set_header directive. To pass on these headers and make information available in places where it is requested.
When Nginx serves as a reverse proxy, it modifies two headers by default. Then remove any empty headers, and forward the request. The Host and Connection headers are the two modified headers. The pertinent ones for reverse proxies will be discussed here later. There are more HTTP headers accessible. You can check this comprehensive list of HTTP headers for more information on each of its purposes.
The headers that proxy_params forwards and the variables that it stores the data in are as follows:
- Host: The website domain and port are the initial hosts that the client requested, and they are contained in this header. This is retained by Nginx in the $http_host variable.
- X-Forwarded-To: The client’s IP address that sent the initial request is contained in this header. It may also include a list of IP addresses, arranged first on the list belonging to the originating client and then all the IP addresses of the reverse proxy servers that sent the request. Nginx stores this in the variable $proxy_add_x_forwarded_for.
- X-Real-IP: The remote client’s IP address is always the only one contained in this header. As opposed to this, the comparable X-Forwarded-For can hold a list of addresses. In the event that X-Forwarded-For is absent, X-Real-IP will apply.
- X-Forwarded-Proto: The protocol—HTTP or HTTPS—that the first client used to establish a connection is contained in this header. This is retained by Nginx in the $scheme variable.
Next, link to the sites-enabled directory that Nginx reads at startup from this configuration file to enable it:
$ sudo ln -s /etc/nginx/sites-available/your_domain /etc/nginx/sites-enabled/
Now you can check for syntactical mistakes in your configuration file:
$ sudo nginx -t
To implement your modifications, restart Nginx if there are no issues reported:
$ sudo systemctl restart nginx
You can now use a local browser to visit Nginx as a reverse proxy for your application server, provided that your application server is up and functioning. You can go ahead and start your desired application server if you already have one but it’s not currently operating. The rest of this tutorial is optional.
If not, move on to the next step and set up a test server and application with Gunicorn.
Step 3: Use Gunicorn to Test Your Reverse Proxy (Optional)
You can now view the application server in your browser if you had it set up and operational before starting this tutorial:

However, you can install Gunicorn and a test application by following the steps below if you don’t have access to an application server to test your reverse proxy. A Nginx reverse proxy is frequently used in conjunction with Gunicorn, a Python WSGI server.
Install gunicorn and update the index of your apt repository:
$ sudo apt update $ sudo apt install gunicorn
For the most recent version, you can alternatively install Gunicorn using pip with PyPI in conjunction with a Python virtual environment; however, apt is being used here as a temporary test bed.
The next step is to create a Python function that will output “Hello World!” in an HTTP response that a web browser can display. Using nano or your favorite text editor, create test.py:
$ nano test.py
Add the subsequent Python code to the document:
def app(environ, start_response):
start_response("200 OK", [])
return iter([b"Hello, World!"])
This is the bare minimum of code that Gunicorn requires to initiate an HTTP response that displays a text string in your browser. Save and exit your file after checking the code.
Now launch your Gunicorn server, being sure to include the app function and the test Python module. When the server is started, your terminal will be taken over:
$ gunicorn --workers=2 test:app

The result verifies that Gunicorn is listening at http://127.0.0.1:8000, which is its default address. This is the address that you previously configured as a proxy for Nginx. If not, return to your file located at /etc/nginx/sites-available/your_domain and modify the app_server_address linked to the proxy_pass argument.
Once your web browser is open, go to the domain you configured using Nginx.
“Hello World!” is being shown by your Gunicorn web application server’s Nginx reverse proxy.
Summarizing about Configure Nginx as a Reverse Proxy on Ubuntu
To sum up, setting up Nginx as a reverse proxy on Ubuntu 22.04. Successfully, is a big step in the right direction for optimizing your web server setup. You may take advantage of Nginx’s powerful capabilities for enhanced security. Load balancing, and performance by following the steps described in this guide.
Upon completion of this configuration process, you will have acquired a useful skill set. That is essential for efficiently managing and scaling web applications. Accept the improved features that Nginx offers to your server architecture. Do use a well-configured reverse proxy solution to negotiate the complex web hosting landscape with confidence. Unlock the full potential of your Rocky Linux server with our manual to mastering Nginx and turn your server into a high-performance powerhouse with just a few commands.
Undestanding all, you have set up Nginx to act as a reverse proxy. Allowing access to your application servers that are only accessible locally. Furthermore, you set up the request header forwarding, transmitting the header data from the client.